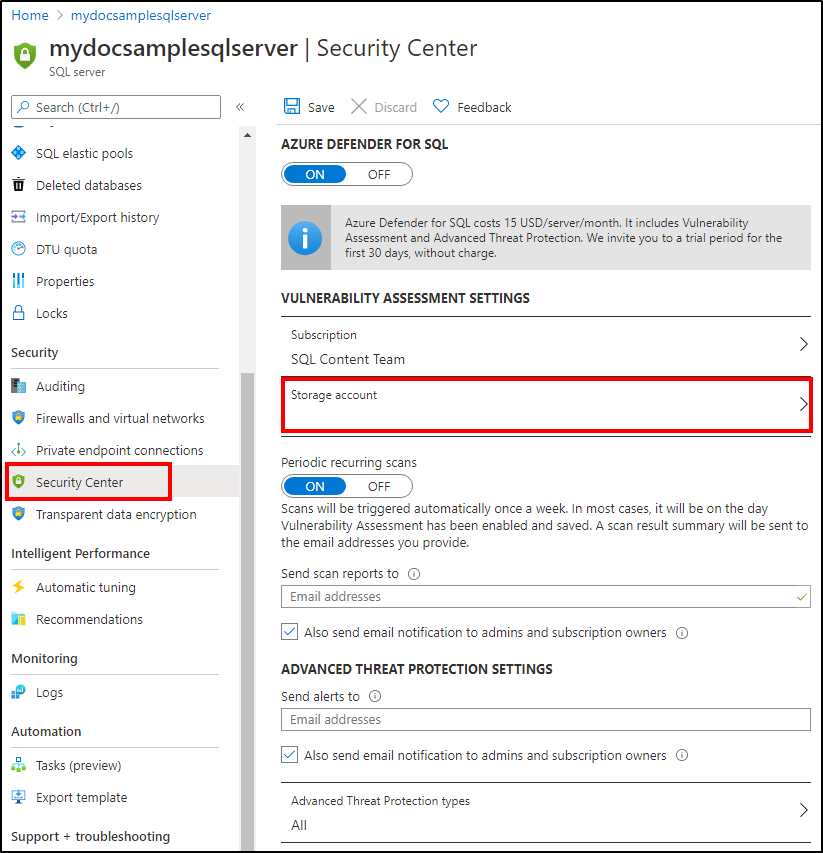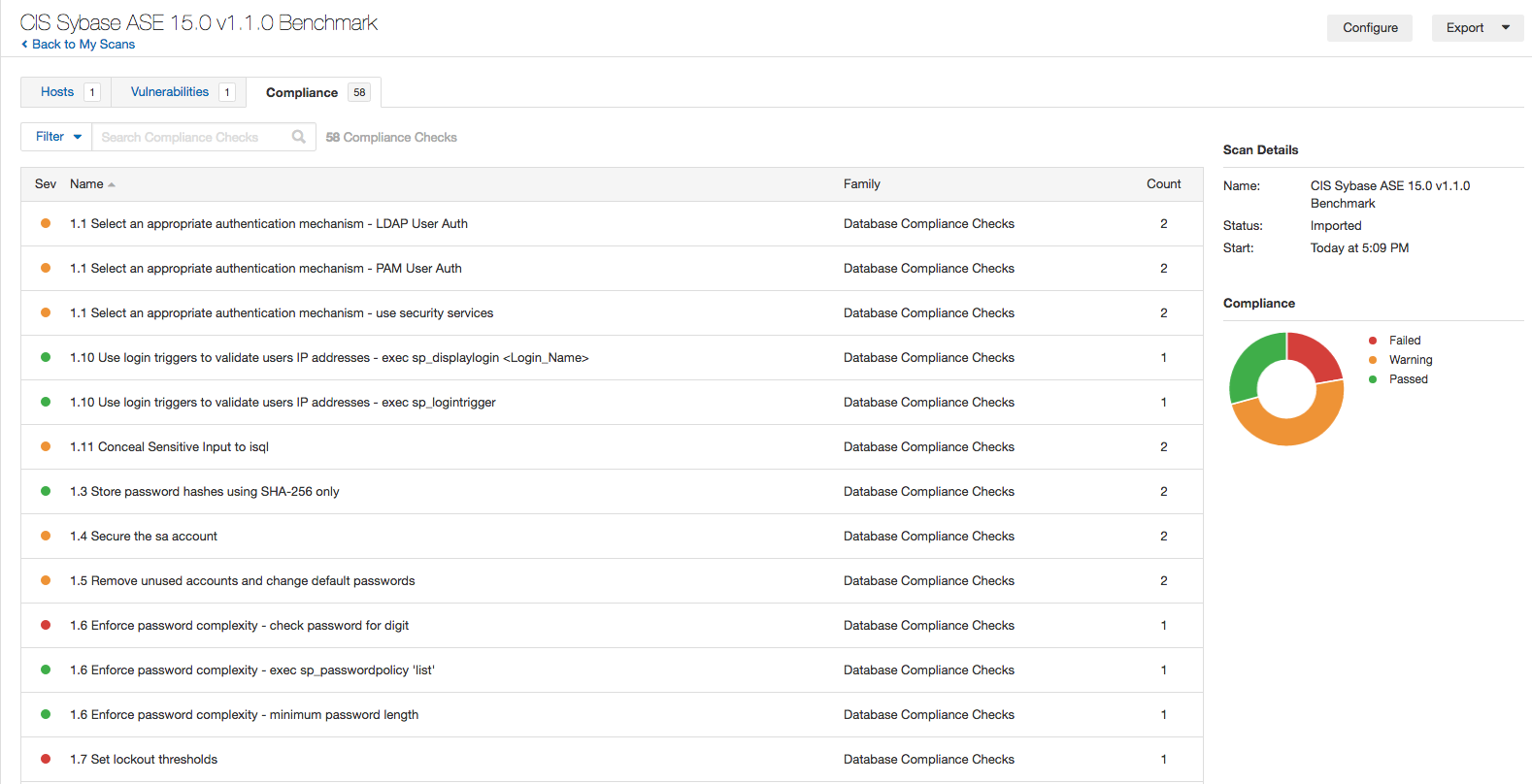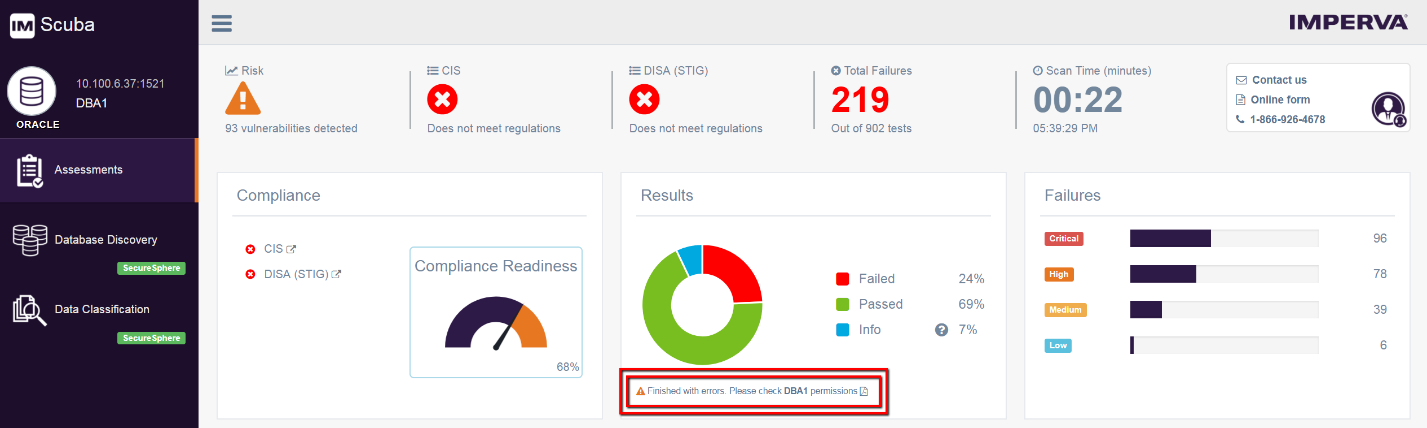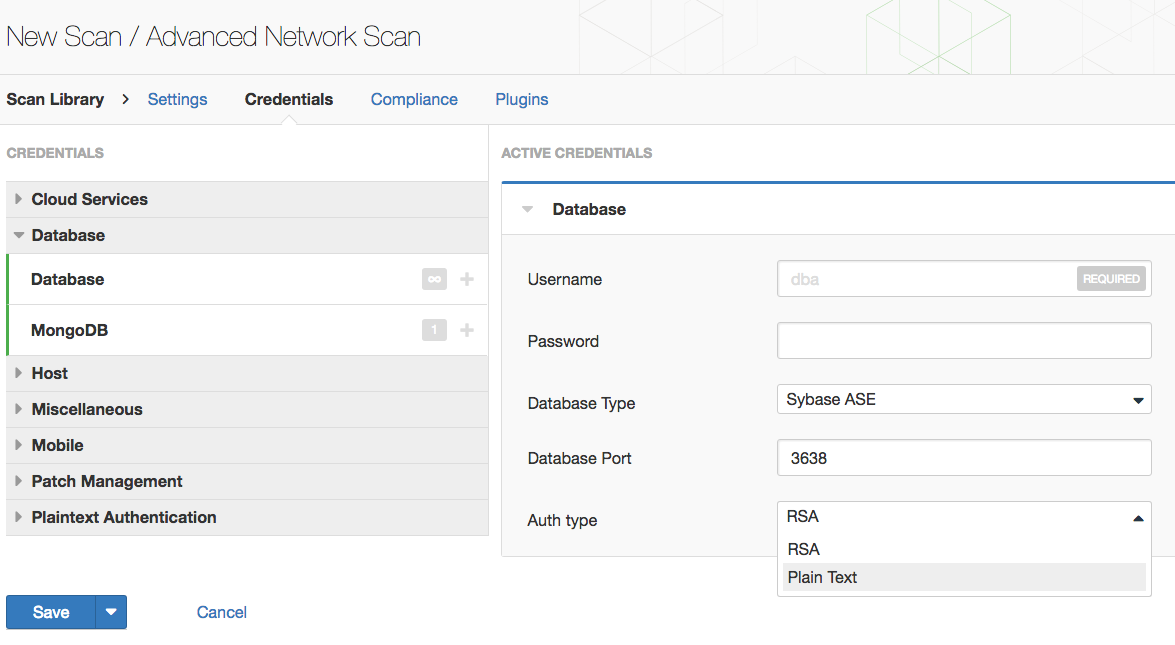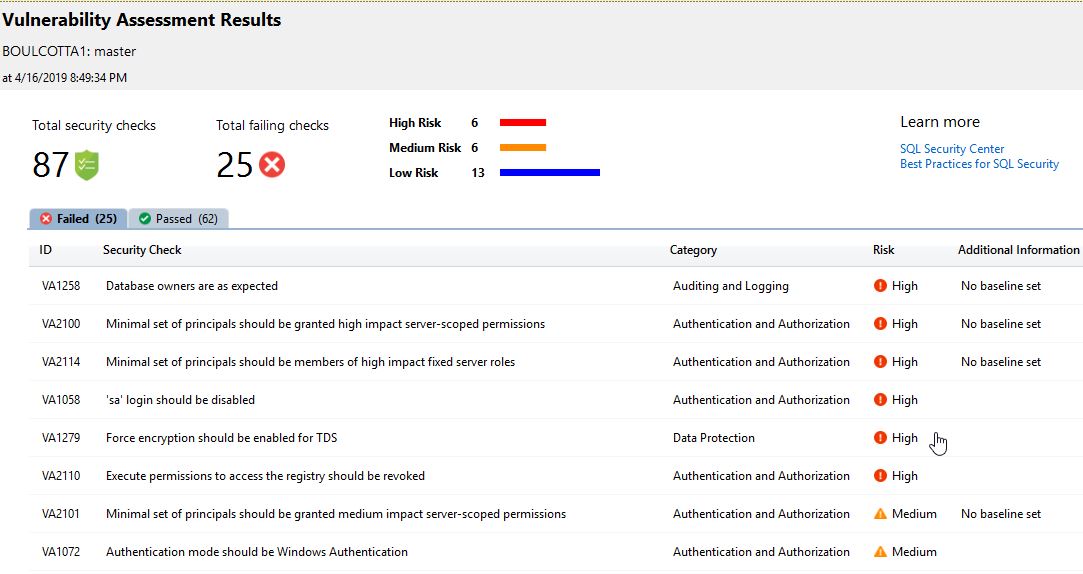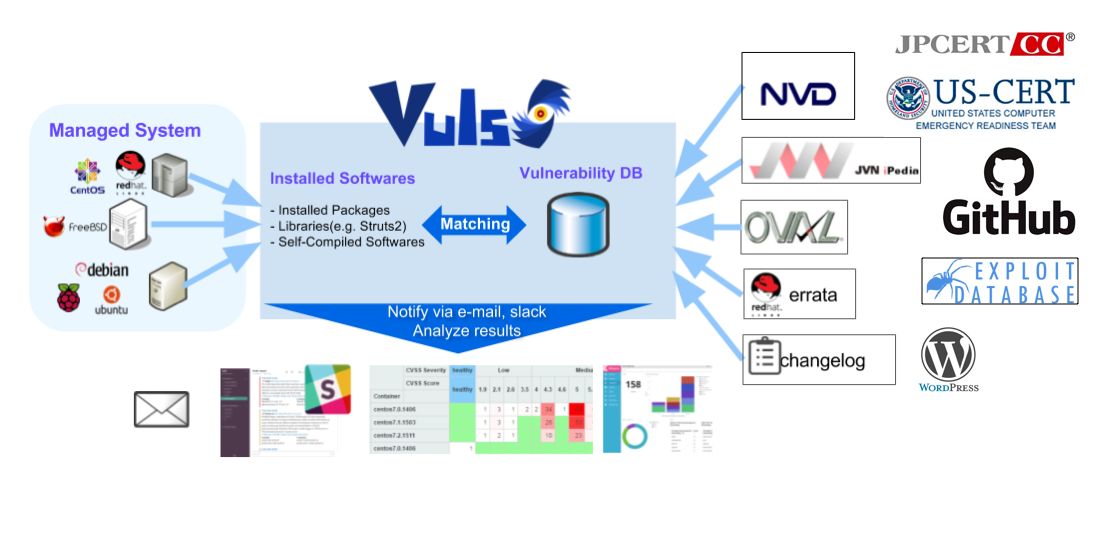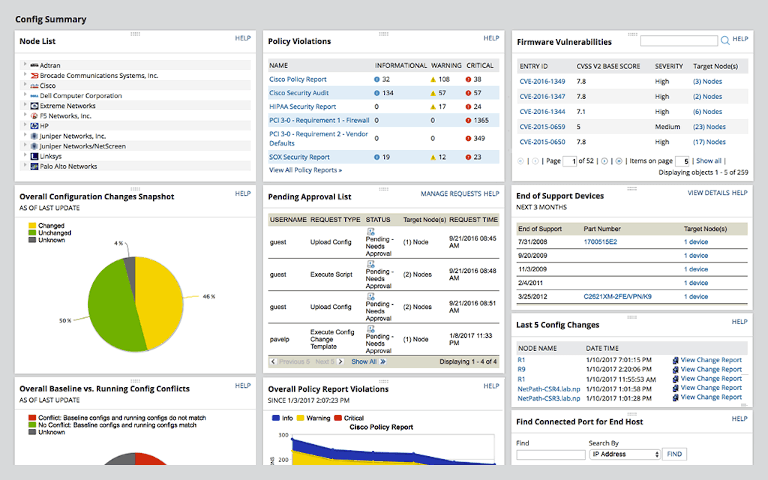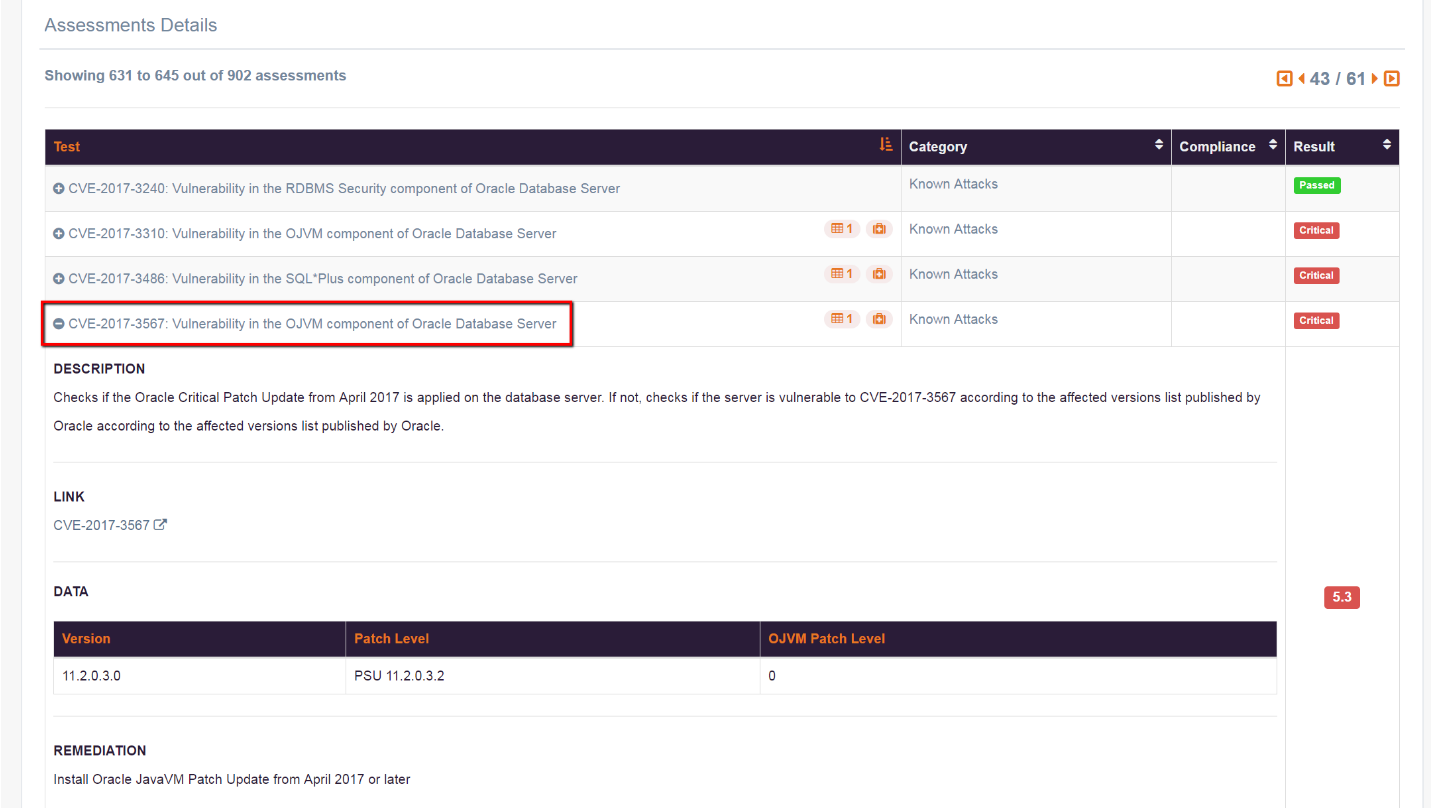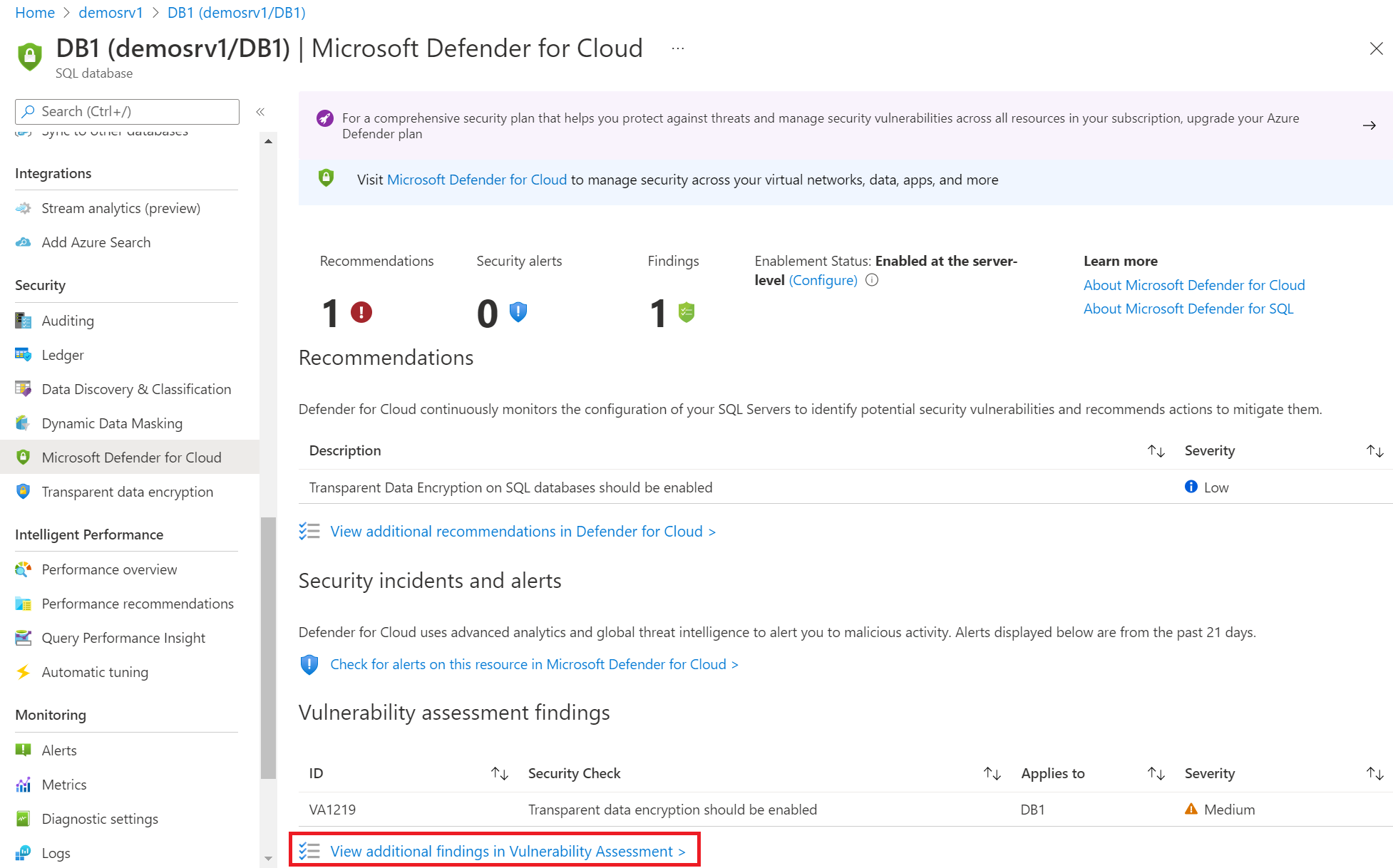
SQL vulnerability assessment - Azure SQL Database & SQL Managed Instance & Azure Synapse Analytics | Microsoft Docs
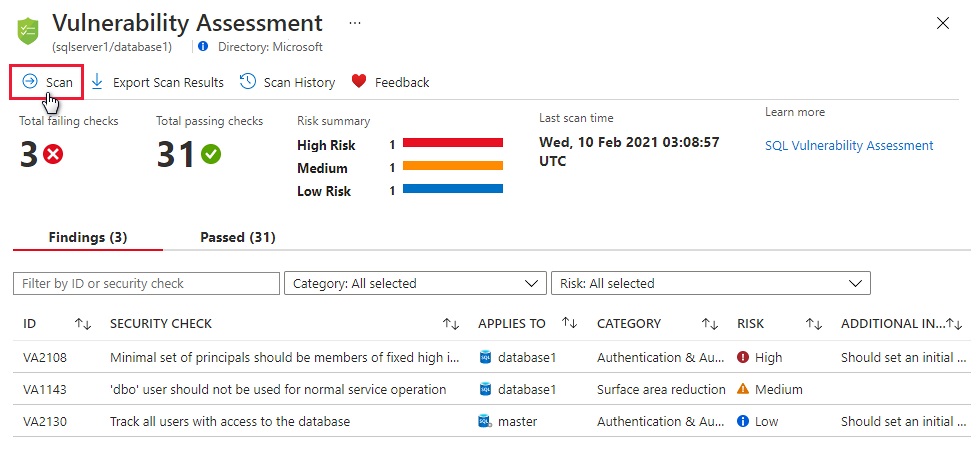
SQL vulnerability assessment - Azure SQL Database & SQL Managed Instance & Azure Synapse Analytics | Microsoft Docs

SQL vulnerability assessment - Azure SQL Database & SQL Managed Instance & Azure Synapse Analytics | Microsoft Docs